Trustfull Email
Overview
Introduction
The Trustfull Email API evaluates email addresses in real time to assess trust and fraud risk. It detects disposable and invalid emails, analyzes domain reputation and digital footprint, and checks identity consistency across sources to identify fake, synthetic, or compromised accounts, providing clear risk signals and reason codes without harming conversion.
Want to learn how to set it up? Visit the dedicated Trustfull Email API Reference.
Below, each section explains:
- What we see in genuine email addresses
- What we see in risky email addresses
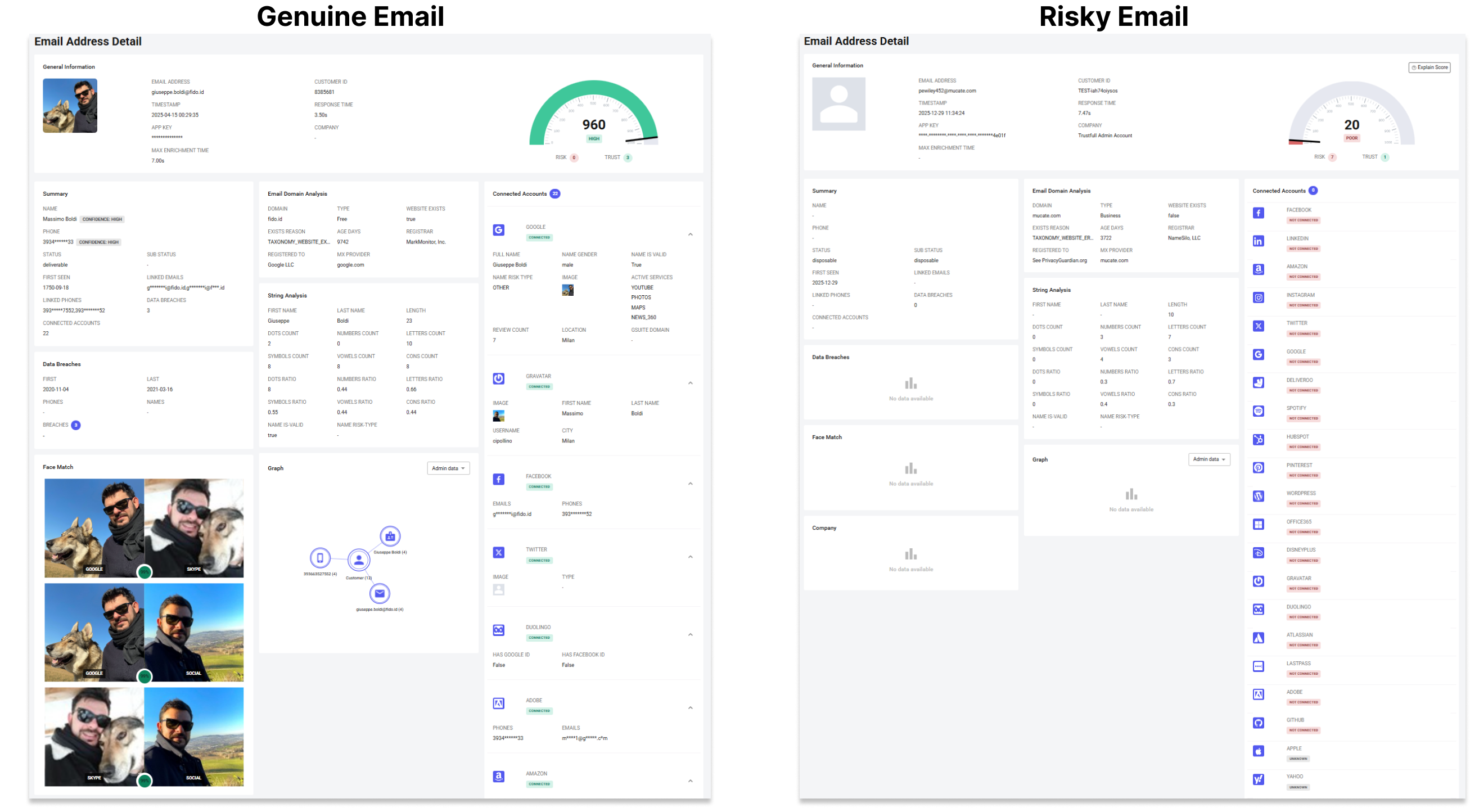
General Information
This section displays general information about the lookup:
- Timestamp: when the API or manual lookup was executed
- App Key: API key used to process the lookup
- Customer ID: proprietary identifier for the customer
- Max Enrichment Time: total number of seconds available for enrichment
- Response Time: time required to retrieve and return the data
This information is mainly used for monitoring, debugging, and auditing API usage.
Score
Genuine Email
- Score:
770/1000| Label:HIGH| Risk Signals:0| Trust Signals:4+
Multiple trust signals with no contradictory behavior and strong consistency across sources make this email safe for low-friction flows.
Risky Email
- Score:
0–450/1000| Label:BAD / LOW| Risk Signals:3+| Trust Signals:0–1
Disposable or invalid emails, newly created addresses, lack of connected accounts, absence of historical digital footprint, or compromised breach patterns commonly drive low scores.
Reason Codes Examples
- Trust codes: Email Regular Velocity | Email With Data Breaches | Email Internal Consistency (Names) | Email Image With Person
- Risk codes: Email Disposable | Email Low Velocity | Email Invalid | Email Without Data Breaches
Curious how the score is calculated? Explore our Reason Codes and the Scoring Methodology and that drives it.
Summary
Genuine Email
- Deliverable email
- High confidence in name and phone consistency across signals
- Multiple connected accounts
- Linked to an established domain
- Historical first-seen date
Real users rely on the same email address across services and over time, which naturally creates domain presence, account reuse, and historical traces that are difficult to fabricate consistently.
Risky Email
- Invalid or disposable
- Low confidence in name and phone consistency across signals
- No domain presence
- No connected accounts
- Very recent creation
Fraudsters prioritize speed and scale over persistence. Disposable or newly created email addresses are optimized for short-lived use, enabling repeated signups while minimizing exposure and traceability.
Email Domain Analysis
Genuine Email
- Well-known or established domain
- Website exists
- Domain age consistent with usage
Established domains are costly to abuse at scale and are usually protected by reputation systems and provider-level controls, making them more likely to belong to legitimate users than to short-lived fraud campaigns.
Risky Email
- Newly registered or parked domain
- No active website
- Very low domain age
- Redirects or placeholder pages
Fraudsters frequently rely on freshly registered or neglected domains because they are cheap, disposable, and difficult to trace, lacking the infrastructure and visibility of legitimate domains.
Email String Analysis
Genuine Email
- Realistic name structure
- Normal length and character distribution
- No excessive numbers or symbols
- Name validity confirmed
Human-created email addresses tend to follow readable, meaningful patterns that emerge naturally over time, unlike automated aliases that leave detectable statistical fingerprints.
Risky Email
- Random or placeholder strings
- Excessive numbers or symbols
- Famous names or generic patterns
- High-risk name classification
Programmatically generated emails favor speed and volume, often sacrificing realism and consistency in favor of easy automation.
Connected Accounts
Genuine Email
- Presence on multiple consumer platforms
- Mix of social, productivity, and media services
- Accounts marked as connected
- Consistent identity attributes
This is important because fraudsters rarely activate multiple consumer services, reuse the same email consistently, or expose real names and photos across platforms.
Risky Email
- No connected accounts
- All services marked as not connected
- No public or private footprint
Disposable emails are intentionally isolated and created to pass a single checkpoint, leaving no downstream activity or service reuse.
Image Analysis
Genuine Email
- Profile images detected
- Human face identified
- Age and gender estimated
- Images consistent across sources
Maintaining a consistent visual identity across platforms requires sustained effort and real-world exposure, which is uncommon in fraudulent identities.
Risky Email
- No images available
- AI-generated or stock images
- Low-quality or reused pictures
- No face detected
Fraud identities minimize exposure to reduce attribution risk and are therefore more likely to avoid or fake visual signals.
Data Breaches
Genuine Email
- One or more breaches present
- Old timestamps
- Realistic breach sources
Most real users appear in at least one breach over time due to widespread incidents affecting legitimate services, making historical exposure normal rather than suspicious.
Risky Email
- No breaches at all
- No historical exposure
- Recently created address
Emails with no breach history are often too new to have been reused meaningfully and become highly indicative of risk when combined with other weak signals.
Graph (Link Analysis)
Genuine Email
- Simple, clean graph
- One email linked to one person
- Limited phones and accounts
- No clustering
This indicates a single real individual. Real identities grow organically, producing small, stable graphs rather than dense or repetitive networks.
Risky Email
- Sparse or fragmented graph
- Weak or artificial connections
- Email isolated from real identities
Disposable or fabricated emails are rarely reused across identity dimensions, resulting in shallow or disconnected graphs.
Face Match
Genuine Email
- Faces detected from multiple sources
- High similarity between images
- Supports identity continuity
Face matching reinforces identity coherence by confirming that visual signals across platforms belong to the same individual.
Risky Email
- No faces available
- Mismatched or unusable images
- Face match not possible
Low-effort or automated identities often lack usable images or intentionally avoid visual consistency.
Company Information
Genuine Business Email
- Company name and logo identified
- Industry and keywords available
- Employee count and age present
Business emails introduce accountability, as public company metadata and operational history make impersonation harder without leaving discrepancies.
Risky Business Email
- No company data available
- Domain unrelated to claimed business
- Placeholder or inactive organization
Fake business emails are often created to bypass B2B controls and typically lack credible company-level signals.
Final Takeaway
A genuine email address:
- Has history
- Has presence
- Has consistency
- Is reused across services
A risky email address:
- Is new or disposable
- Lacks digital footprint
- Shows artificial patterns
- Exists only to pass signup checks
Trustfull Email is designed to separate these two profiles in real time, enabling accurate fraud detection without harming legitimate users.
📚 Resources
- Support Center — Assistance and answers from the Trustfull team.
- Trustfull Email API Reference page — Technical guidance on setup.
Updated 20 days ago