Trustfull IP
Overview
Introduction
Trustfull IP analyzes IP addresses in real time to assess whether a connection originates from a legitimate user or from anonymized, automated, or high-risk infrastructure.
Rather than relying on static blocklists alone, Trustfull IP evaluates geolocation accuracy, network type, masking techniques, blacklist reputation, and cross-signal consistency, producing a clear trust score that helps identify VPN usage, proxy traffic, bot activity, and suspicious access patterns without blocking legitimate users.
Want to learn how to set it up? Visit the dedicated Trustfull IP API Reference.
Below, each section explains:
- What we see in genuine IP connections
- What we see in risky IP connections
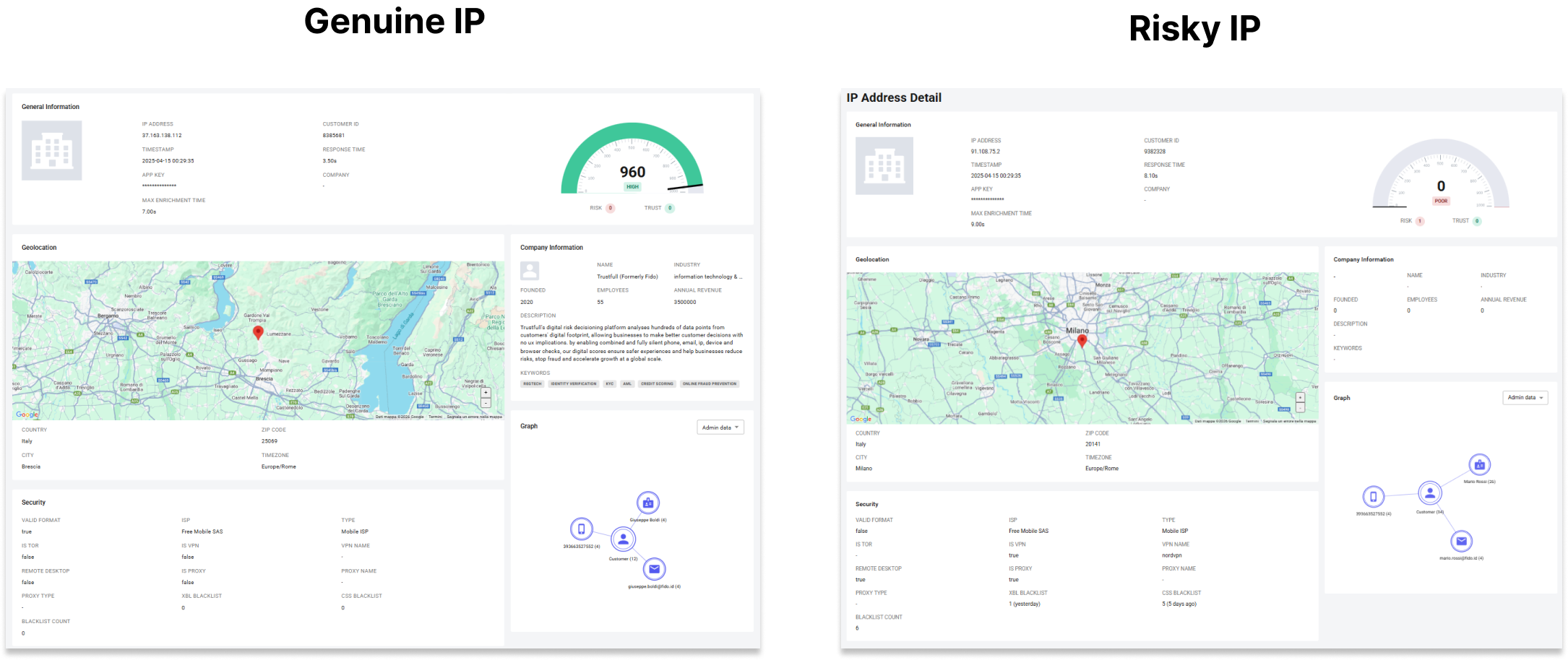
General Information
This section displays general information about the IP lookup:
- Timestamp: when the lookup was executed
- App Key: API key used to process the request
- Customer ID: proprietary identifier for the customer
- Max Enrichment Time: total time allocated for IP enrichment
- Response Time: time required to retrieve and return the result
This information is mainly used for performance monitoring, auditing decisions, and debugging integration issues.
Score
Genuine IP
- High score | Label:
GOOD / HIGH| Risk Signals:0| Trust Signals:1+
A high score indicates that the IP originates from a trusted network, shows no signs of masking or automation, and aligns geographically and technically with normal user behavior.
Risky IP
- Low score | Label:
LOW / POOR| Risk Signals:2+| Trust Signals:0
Low scores typically emerge when IPs show anonymization techniques, suspicious network origins, or behavior commonly associated with automation or abuse.
Reason Codes Examples
- Trust codes: IP Regular Connection | IP Regular Connection | IP Regular Connection
- Risk codes: IP Masking (Proxy) | IP Masking (VPN) | IP Masking (TOR) | IP Blacklisted
Curious how the score is calculated? Explore our Reason Codes and the Scoring Methodology and that drives them.
Geolocation
Genuine IP
- Country, city, and timezone resolved
- Location consistent and stable
- Geography aligns with other identity signals
Legitimate users typically connect from predictable geographic areas, and their IP location aligns naturally with language, timezone, and other identity attributes.
Risky IP
- Inconsistent or unstable geolocation
- Country mismatches across sessions
- Location conflicts with other signals
Unstable or conflicting geolocation often indicates routing through anonymization infrastructure or automated traffic rather than normal residential usage.
Security
Genuine IP
- Residential or mobile network
- No VPN, proxy, or Tor detected
- No blacklist reputation
Most real users connect through standard ISPs or mobile networks, which exhibit normal routing behavior and are rarely associated with abuse infrastructure.
Risky IP
- VPN, proxy, or Tor detected
- Datacenter or hosting infrastructure
- Blacklist presence or abuse history
Anonymization and hosting infrastructure are frequently used to conceal origin, bypass controls, or automate activity, making them strong indicators of elevated risk.
Company Information
Genuine IP
- IP range linked to a known ISP or organization
- Organization type clearly identified
Matching IP blocks to known organizations adds accountability and reduces ambiguity around traffic origin.
Risky IP
- No company attribution
- Infrastructure linked to hosting or cloud providers
Anonymous or generic infrastructure makes attribution difficult and is commonly associated with automated or abusive traffic.
Graph (Link Analysis)
Genuine IP
- IP linked to a small number of identities
- Consistent relationships across signals
- No repetition or clustering
Legitimate IP usage produces simple graphs reflecting organic access patterns rather than shared infrastructure.
Risky IP
- IP linked to many identities
- Repeated reuse across emails or phones
- Dense or artificial connection patterns
Shared IP infrastructure is a common characteristic of bot networks, fraud rings, and account farming operations.
Final Takeaway
A genuine IP address:
- Comes from residential or mobile networks
- Has stable geolocation
- Shows no masking or blacklist signals
- Aligns with other identity attributes
A risky IP address:
- Uses VPN, proxy, or Tor infrastructure
- Originates from datacenters or hosting providers
- Shows abuse or blacklist history
- Conflicts with other identity signals
Trustfull IP is designed to distinguish these patterns in real time, enabling adaptive fraud prevention without blocking legitimate users.
📚 Resources
- Support Center — Assistance and answers from the Trustfull team.
- Trustfull IP API Reference page — Technical guidance on setup.
Updated 27 days ago