Trustfull Phone
Overview
Introduction
The Trustfull Phone API evaluates phone numbers in real time to assess trust and fraud risk. It detects VoIP and virtual numbers, validates line type and country, and analyzes reputation and usage patterns to identify fake or abusive activity, providing clear risk signals and reason codes to protect signups, logins, and transactions without harming conversion.
Want to learn how to set it up? Visit the dedicated Trustfull Phone API Reference.
Below, each section explains:
- What we see in genuine phone numbers
- What we see in risky phone numbers
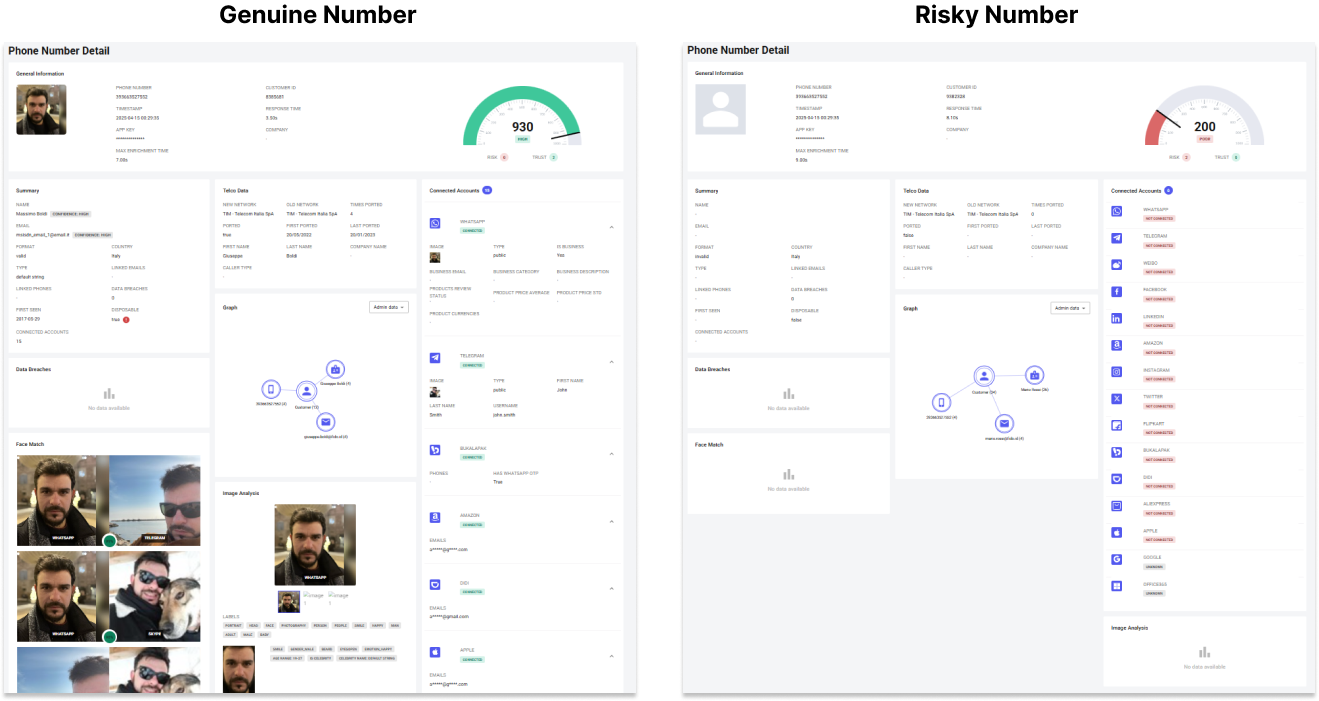
General Information
This section displays some general information about the lookup:
- Timestamp: when was the API or manual lookup made
- App Key: API key used to process the lookup
- Customer ID: proprietary ID used to identify the customer
- Max Enrichment Time: Total number of seconds available for the data enrichment
- Response time: How long it took to retrieve the data and respond
Score
Genuine Number
- Score:
980/1000| Label:HIGH| Risk Signals:0| Trust Signals:4
Why this matters: Multiple trust signals with no contradictory behavior and strong consistency across sources make this number safe for low-friction flows.
Risky Number
- Score:
0–400| Label:LOW| Risk Signals:5| Trust Signals:1
Common causes: Disposable/VOIP numbers, recently issued, no historical digital footprint, or abuse-related telco patterns.
Reason Codes Examples
- Trust codes: Email Regular Velocity | Email With Data Breaches | Email Internal Consistency (Names)
- Risk codes: Email Disposable | Email Low Velocity | Email Invalid | Email Without Data Breaches
Curious how the score is calculated? Explore our Reason Codes and the Scoring Methodology and that drives it.
Summary
Genuine Number Characteristics
| Signal | Value (example) |
|---|---|
| Name | Present, high confidence |
| Format | Valid |
| Type | Mobile |
| Country | Italy |
| First Seen | 2021 |
| Disposable | False |
| Data Breaches | 1 |
| Connected Accounts | 7 |
Interpretation:
- Real users leave long-term digital traces
- One historical breach is normal for real people
- Multiple connected accounts indicate legitimacy
Risky Number Characteristics
| Signal | Value (example) |
|---|---|
| Name | Missing or low confidence |
| None | |
| First Seen | very recent |
| Disposable | True |
| Data Breaches | 0 |
| Connected Accounts | none |
Fraud numbers are optimized for short-lived use, not long-term identity as they typically lack connected accounts, have no porting history, show no data breach presence, and are often flagged as disposable or recently issued.
Telco Data
Genuine Number
- Safe carrier with KYC procedures
- Ported in the past
- Regular porting history (e.g. 1 or 2 times)
- Matches geographic context
Porting alone is not suspicious when it happened long ago, occurs infrequently, and is accompanied by other strong trust signals. The presence of porting history in a genuine number typically indicates normal carrier switching behavior rather than fraudulent activity.
Risky Number
- Very recent porting or no porting at all
- Multiple ports in short time
- Virtual or high-risk carriers with low KYC
- SIM-swap–prone patterns
These patterns are commonly associated with account takeover, OTP interception, and financial fraud. Fraudsters exploit weak carrier controls and rapid porting capabilities to gain unauthorized access to accounts and bypass security measures.
Connected Accounts
Genuine Number
- Connected to multiple major platforms (Telegram, Facebook, WhatsApp, Amazon, Instagram, Google, Office365)
- Real names and profile images
- Consistent identity across platforms
This is important because fraudsters rarely activate multiple consumer services, reuse the same phone consistently, or expose real names and photos.
Risky Number
- No connected accounts
- No messaging apps
- No profile image
- Recently created accounts
Often used only for OTP reception, account farming, and abuse automation.
Data Breaches
Genuine Number
- One/few historical breaches
- Old timestamp
- Real name present
Most real users appear in at least one breach over time.This is normal and expected, not a fraud signal by itself.
Risky Number
- No breaches at all
- Extremely hush number of data breaches
This is beacuse disposable or fraudolent numbers are usually too new, and therefore not present in historical datasets.
Image Analysis
Genuine Number
- Profile image detected
- Clear human face
- Age range estimated
- Accessories, clothing, emotion detected
- High-quality real-world photo
This indicates a real person with a long-lived social presence and high-quality identity.
Risky Number
Typical findings:
- No images
- Stock photos
- AI-generated faces
- Low-resolution or reused images
- No face detected
Fraud identities minimize exposure and traceability by deliberately avoiding profile pictures, using generic or AI-generated images, and maintaining minimal digital presence to reduce the risk of detection and attribution across platforms.
Links Analysis
Genuine Number
- Small, clean graph
- Consistent identity across phone, email, and name
- No suspicious clustering
This indicates one real person, not a network. Link analysis reveals consistency: real users maintain a small, stable cluster of connected identifiers, whereas fraudsters create sprawling networks where one email controls dozens of phones—patterns structurally impossible for legitimate individuals.
Risky Number
- Dense graphs
- Many phone numbers linked to the same email or device
- Repeated patterns
These patterns are commonly seen in bot networks, fraud rings, and account farms—organized operations designed to create fake accounts at scale.
Final Takeaway
A genuine phone number:
- Has history
- Has presence
- Has consistency
- Looks in use across multiple dimensions
A risky phone number:
- Is new
- Is disposable
- Has no digital footprint
- Not used or inactive
Trustfull Phone is designed to separate these two profiles in real time, enabling adaptive fraud prevention without harming legitimate users.
📚 Resources
- Support Center — Assistance and answers from the Trustfull team.
- Trustfull Phone API Reference page — Technical guidance on setup.
Updated 27 days ago