Trustfull Onboarding
Overview
Trustfull Onboarding evaluates user identity at signup in real time by combining multiple Trustfull products into a single holistic score. It analyzes cross-product consistency across email, phone, IP to detect identity theft, synthetic identities, and social engineering attempts without harming conversion.
Want to learn how to set it up? Visit the dedicated Trustfull Onboarding API Reference.
Below, each section explains:
- What we see in genuine onboarding attempts
- What we see in risky onboarding attempts
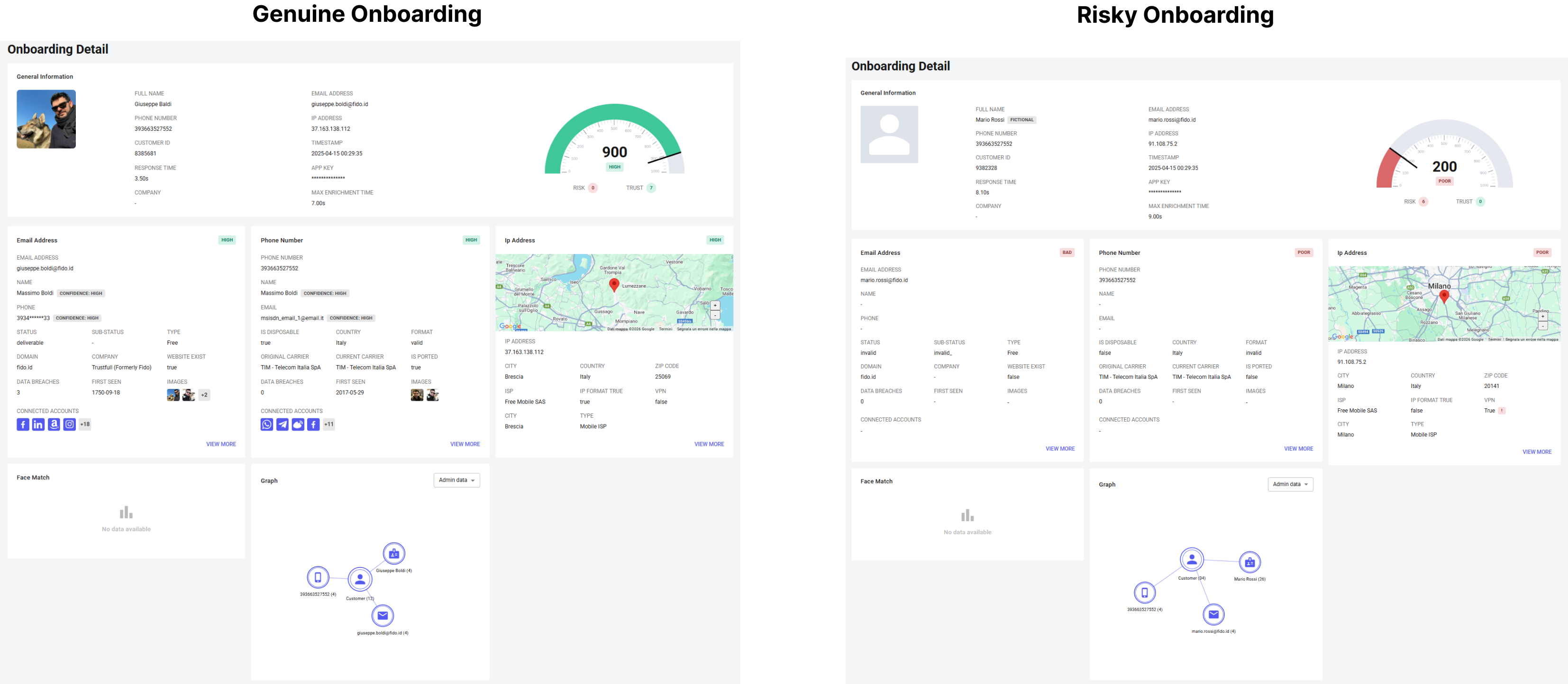
General Information
This section displays general information about the onboarding lookup:
- Timestamp: when the onboarding check was executed
- App Key: API key used to process the request
- Customer ID: proprietary identifier for the customer
- Max Enrichment Time: total number of seconds allocated to enrich all signals
- Response Time: time required to retrieve and aggregate all results
This information helps monitor performance, audit decisions, and debug onboarding workflows.
Score
Genuine Onboarding
- High score (
800–1000) | Label:HIGH| Risk Signals:0| Trust Signals:5+
A high onboarding score indicates that individual signals are not only legitimate but also mutually consistent. Real users tend to present stable identity attributes that align naturally across email, phone, IP, images, and behavioral context.
Risky Onboarding
- Low score (
0–400) | Label:LOW / POOR| Risk Signals:3+| Trust Signals:0–1
Low scores often emerge when signals pass basic validation but fail to connect meaningfully. This pattern is typical of synthetic or manipulated identities, where elements are assembled to look legitimate in isolation but lack real-world linkage.
Reason Codes Examples
- Trust codes: Email Phone Consistency | Email Phone Faces Match | Email Name Consistency | IP Regular Connection
- Risk codes: Email And Phone Inconsistency | Email Phone Faces No Match | IP Masking (VPN) | Name Invalid
Curious how the score is calculated? Explore our Reason Codes and the Scoring Methodology and that drives it.
Email Address
Genuine Email
- Deliverable email
- High confidence in name and phone consistency across signals
- Multiple connected accounts
- Linked to established domain
- Historical first-seen date
Real users rely on the same email address over long periods and across multiple services. This longevity produces domain presence, connected platforms, and historical traces that are difficult for fraudsters to replicate consistently.
Risky Email
- Invalid or disposable
- Low confidence in name and phone consistency across signals
- No domain presence
- No connected accounts
- Very recent creation
Fraudsters prioritize speed and scale over persistence. Disposable or newly created email addresses are optimized for short-lived use, enabling repeated signups while minimizing exposure and traceability.
Phone Number
Genuine Phone
- Valid mobile format
- High confidence in name consistency across signals
- Country and carrier consistent
- Historical footprint
- Connected consumer services
Phone numbers are high-friction identity attributes. Real users tend to reuse the same number across time and platforms, building history, service connections, and consistent carrier information.
Risky Phone
- Invalid format or disposable
- Low confidence in name and email consistency across signals
- No historical presence
- No connected accounts
Fraud-related phone numbers are often acquired for temporary use. They are rarely reused, lack history, and show minimal presence on external services.
IP Address
Genuine IP
- Residential IP
- No VPN, proxy, or Tor detected
- Stable geolocation
- Country consistent with phone and email
Legitimate users typically access services from predictable network environments. Residential IPs align geographically with other identity attributes, reinforcing the authenticity of the onboarding attempt.
Risky IP
- VPN, proxy, or Tor traffic
- Masked or unstable location
- Country mismatches
Anonymization techniques are frequently used to obscure origin, automate abuse, or bypass geo-based controls. When IP data conflicts with other identity signals, it strongly suggests intentional concealment.
Link Analysis
Genuine Onboarding
- Few connections: one person, one email, one phone
- Name consistency across signals
- No clustering or repetition
Real individuals form simple, interpretable identity graphs centered around themselves. The absence of dense connections reflects organic, non-scaled behavior.
Risky Onboarding
- Dense or repetitive graphs with shared phones or emails
- Name inconsistency across signals
- Multiple identities linked together
Fraud operations rely on reuse and scale. Dense graphs expose shared infrastructure and coordinated activity that is extremely unlikely for legitimate users.
Face Match
Genuine Onboarding
- Profile images detected
- Faces extracted from multiple sources
- Images match the same individual
Maintaining consistent visual identity across platforms requires sustained effort and real-world exposure. Fraudsters rarely expose real faces or reuse images consistently, making face continuity a strong authenticity signal.
Risky Onboarding
- No images or unusable images
- AI-generated or stock photos
- Faces do not match across sources
Fraud identities minimize exposure to avoid attribution. Missing, artificial, or inconsistent images often indicate deliberate obfuscation rather than a legitimate lack of data.
Final Takeaway
A genuine onboarding attempt:
- Shows consistency across signals
- Reinforces identity through cross-checks
- Has history and reuse
- Forms a simple, coherent identity graph
A risky onboarding attempt:
- Passes checks in isolation but fails in combination
- Shows mismatches across email, phone, IP, or images
- Lacks real-world linkage
- Reveals scaled or synthetic patterns
Trustfull Onboarding is designed to surface these inconsistencies in real time, enabling accurate identity risk assessment without penalizing legitimate users.
📚 Resources
- Support Center — Assistance and answers from the Trustfull team.
- Trustfull Onboarding API Reference page — Technical guidance on setup.
Updated 27 days ago