Links Analysis
What is Links Analysis?
Links Analysis is a groundbreaking feature designed to establish powerful and reliable connections between various digital identifiers. By weaving a web of associations, Trustfull can now pinpoint unusual patterns and identify potentially suspicious activities related to new signups, transactions, or logins.
Why is it a Game-Changer?
This feature addresses the constantly evolving challenges in the digital market, where identity theft and fraudulent activities are becoming increasingly sophisticated. Graph allows Trustfull to transcend traditional silos and connect the dots across multiple identifiers, enabling a more comprehensive and nuanced understanding of user behavior.
How Does It Work?
Links Analysis works by consolidating and linking various pieces of user information across different digital touchpoints to create a unified and comprehensive profile of an individual's online identity. It connects data such as email addresses, phone numbers, device IDs, IP addresses and other identifiers associated with a single user in the Graph.
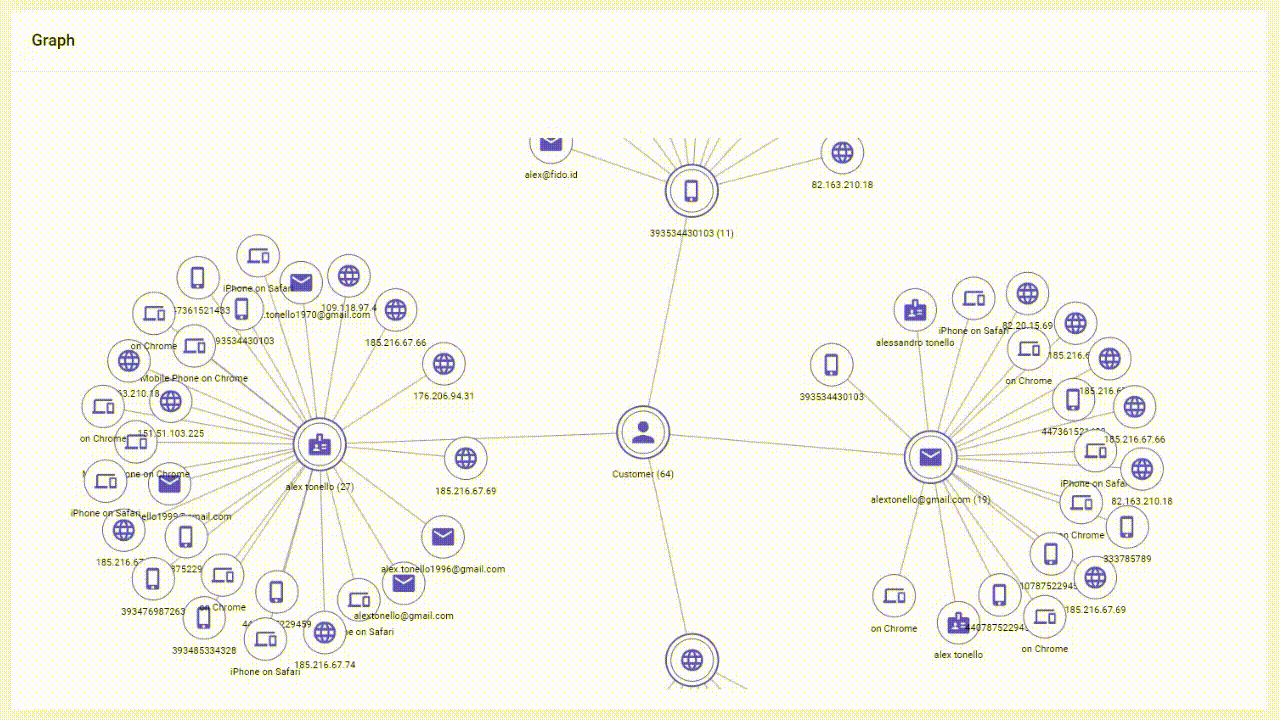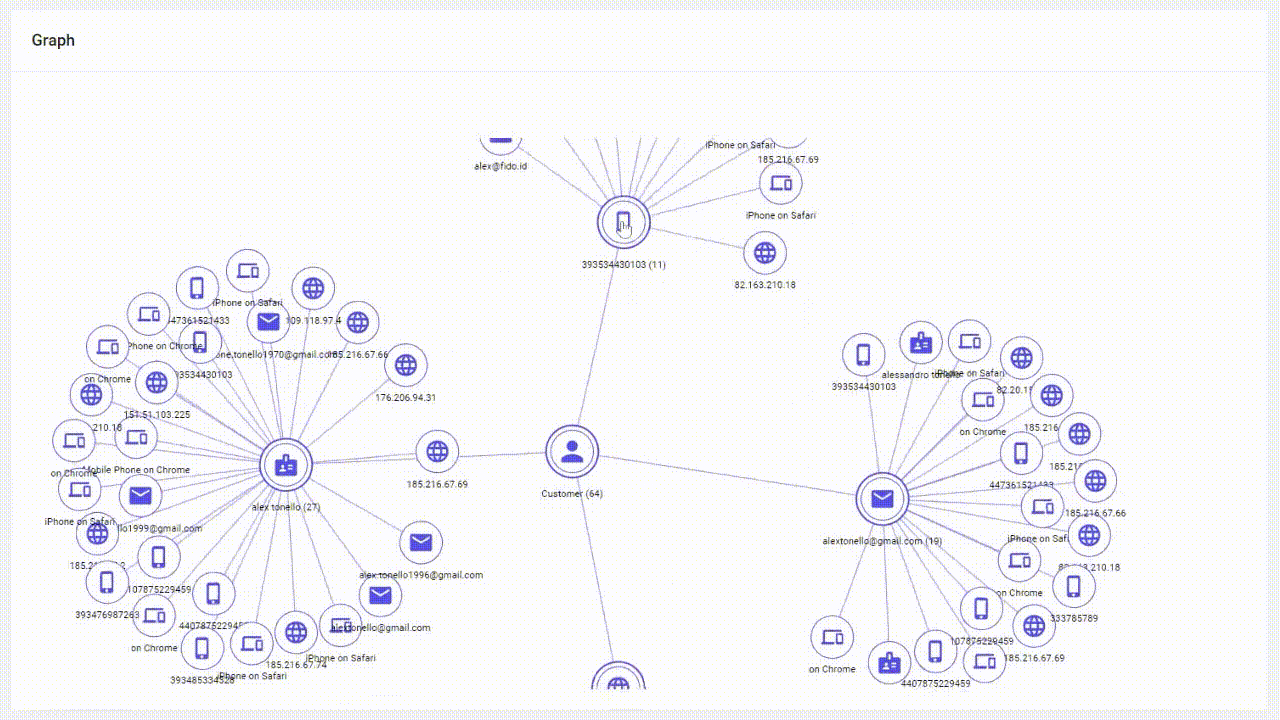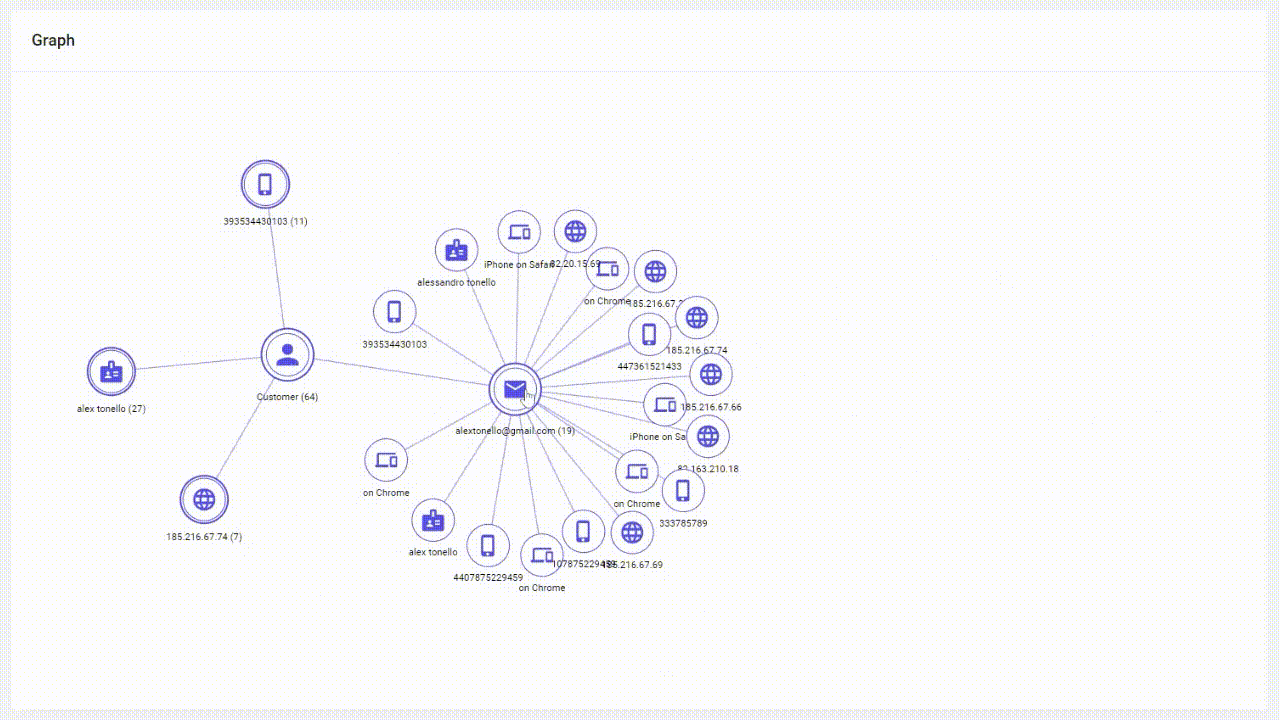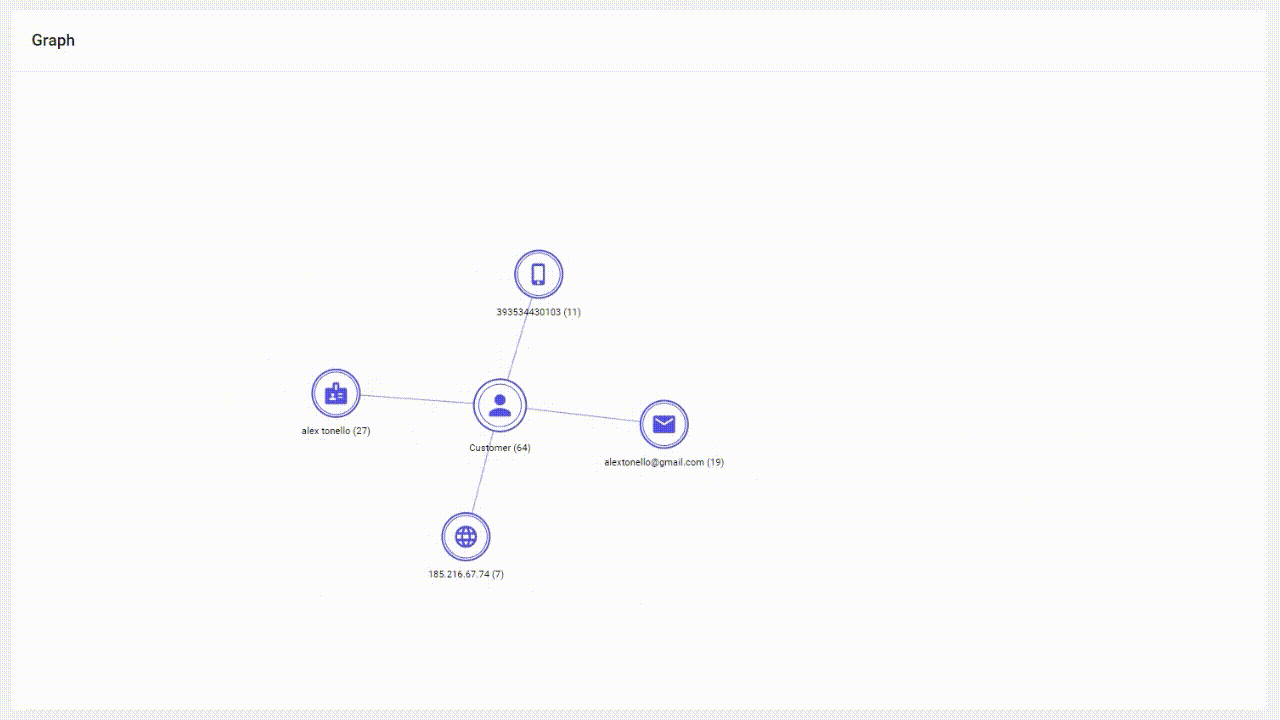
Graph plays a crucial role in authentication and fraud detection processes. By analyzing all digital signals organizations can establish a baseline of normal activity for each user. Any deviations or anomalies from these established patterns can raise red flags and trigger additional verification steps to confirm the user's identity.
Moreover, the use of machine learning and advanced analytics in conjunction with Graph allows for the development of predictive models. These models can identify potential fraud based on historical data and continuously adapt to evolving fraud patterns. By leveraging the comprehensive user profiles created through Graphs, businesses can implement multi-factor authentication, real-time monitoring, and other security measures to enhance fraud prevention efforts and protect against various online threats.
Key Benefits of Graph:
There is a wide range of online fraud types that are creating obstacles for many businesses. Unlocking the following benefits is the next step in building more confidence toward tackling these obstacles:
Holistic view
Graph provides a holistic view of a user's digital footprint by linking diverse identifiers like email addresses, social media accounts, and device information. Valuable data is instantly uncovered for accurate email verification and device detection. As a result, the system either recognizes trust signals giving you an “all-clear” or it raises red flags immediately if synthetic identities are indicated. This comprehensive perspective enhances the accuracy of threat detection.
Pattern recognition
By analyzing the connections between various identifiers, Trustfull can now detect patterns that might go unnoticed through conventional methods. With this approach, the platform isolates and reveals unusual behaviors and potential security threats.
Real-time alerts
Graph operates in real time, generating instant alerts when it detects suspicious activities or deviations from normal user behavior. The objective here is to unlock the ability to take swift action, bolstering the platform's security measures and adding a strong layer to your fraud prevention strategy.
Updated 7 days ago